If you are reading this, you most likely have an interest in network security and some of the protocols used to transport network traffic. QUIC (Quick UDP Internet Connection) is a relatively new protocol gaining rapid adoption due to its use by the FAANGs for streaming and data transfer over the web. Initially, created by Google and deployed as early as 2014, the QUIC protocol was standardized by the Internet Engineering Task Force (IETF) in 2016. Today, QUIC is taking the internet by storm.
QUIC (Quick UDP Internet Connections) is a transport layer protocol that is quickly being adopted across the internet and is a default standard for Google’s Chrome browser. As with most changes, the goal is always to improve upon user experience. Service providers understandably want to provide the most efficient networks to their customers, but with new technology come new challenges, especially in the realm of cyber security.
How QUIC Works
The way QUIC works is by replacing the communication flow components previously handled in TLS and TCP with QUIC and UDP. QUIC has replaced TCP mechanisms such as loss recovery, connection control and connection establishment. QUIC has also absorbed the TLS security layers.
The connection establishment is improved significantly in QUIC where the TLS handshake and TCP handshake are performed within the QUIC protocol. This results in fewer round trips between the communicating devices thus increasing the speed of interactions.
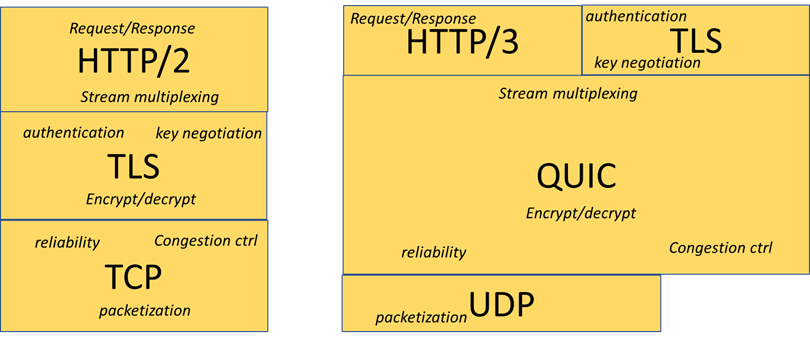
The way QUIC works is by replacing the communication flow components previously handled in TLS and TCP with QUIC and UDP. QUIC has replaced TCP mechanisms such as loss recovery, connection control and connection establishment. QUIC has also absorbed the TLS security layers. The connection establishment is improved significantly in QUIC where the TLS handshake and TCP handshake are performed within the QUIC protocol. This results in fewer round trips between the communicating devices thus increasing the speed of interactions.

Interested in how QUIC-based metadata can be used to detect IoCs?
The QUIC protocol introduces improved security by encrypting everything in the transport layer and not relying on TLS or TCP encryption. This additional security measure was added to eliminate the vulnerabilities that the TCP layer may provide for bad actors.
Top drivers for QUIC adoption:
- Lower Latency
- Better Loss Response
- Security and Privacy
- Extensibility
These enhancements are certainly welcomed in the pursuit of optimized network communications but it’s not without its flaws and concerns from threat hunting teams.
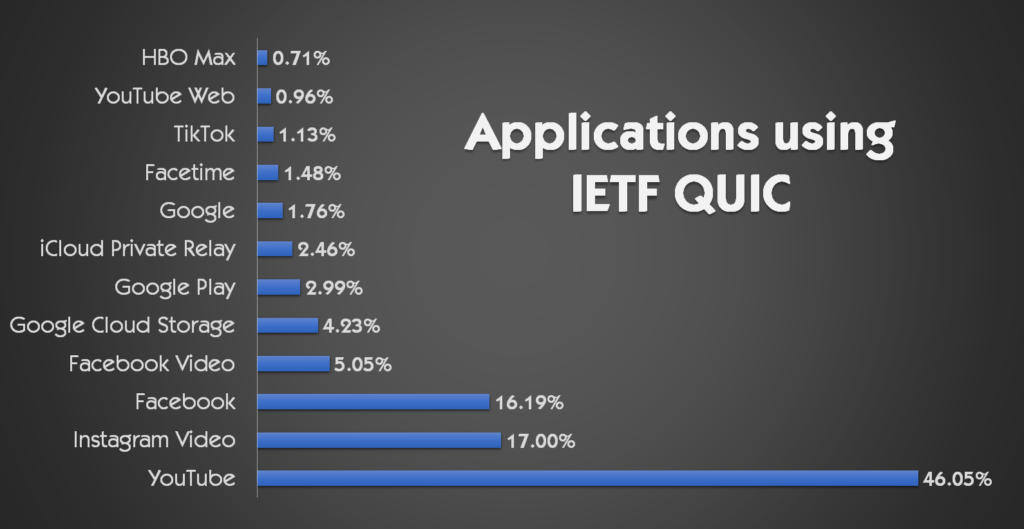
QUIC's Massive Growth
Adoption of the QUIC protocol is growing rapidly. On the client side, Google Chrome, Google App Clients and Facebook’s app support QUIC by default. Safari, Edge, and Firefox support QUIC although it must be enabled by the user today.
From the server side, QUIC is spreading at a fast and furious pace. Google, Microsoft, Facebook, Apple, Akamai, Fastly, Cloudflare and NGINX are all supporting QUIC deployments.
Challenges for Threat Hunting
We here at NetQuest brought the potential issues to light in the past, and now we are getting a more clear picture on what issues the QUIC protocol can pose.
A major fundamental issue that arises when it comes to new technologies is the adoption and adaptation of current security tools. The elimination of TLS session keys makes it more difficult to inspect incoming packets. If QUIC is going to increasingly be used throughout the internet, security products need to cover all their bases and be able to quickly identify these differences when inspecting real-time traffic.
DDoS defense strategies need to be updated as well. Packet identification, inspection and even recording is tougher with the QUIC protocol but TCP syncookies are now replaced with what are called Retry Packets. This can be managed but it does require development and reconfiguration for many security teams. However there is a new type of DDoS attack that has arrived with the QUIC protocol introduction.
QUIC Flood DDoS Attacks
Hackers always look for and usually are successful in finding ways to leverage even the newest of technologies for wrongdoing. A new type of DDoS attack that is being observed are QUIC Floods. This is similar to what we previously knew as UDP flood attacks but they are not the same.
Flood attacks are when an attacker overwhelms a targeted server with an immense amount of spoofed data, forcing the server to attempt to process the overload of data being ingested. This results in the slowing down and sometimes complete crash of said service for consumers.
UDP flood attacks have been around for a long time and security teams have a better understanding of how to handle these attacks. QUIC floods however are unique in that they use UDP underneath it. A QUIC attack would add an extra layer of encryption overtop UDP that would be more difficult for a server to tell whether it is legitimate or a spoof.
Identifying QUIC
Security teams need to update their network security strategy by including the newfound problems the QUIC protocol could present. NetQuest Corporation is helping in the pursuit of identifying and logging QUIC specific metadata.
The NetQuest Network Security Broker (NSB) can classify QUIC and TLS handshakes, forwarding key IP packet header information while truncating encrypted IP payloads utilizing advanced packet inspection algorithms.
The NetQuest Streaming Network Sensors (SNS) includes details encrypted traffic analysis algorithms and can identify powerful Indicators of Compromise (IoC) based on network protocols such as SSH, TLS and QUIC. Teams can use the IoCs exposed by the SNS to detect real-time traffic patterns that match known cyber threats.
Reach out to NetQuest Corporation today to see how you maximize visibility into QUIC traffic and optimize you.