TCP — Transmission Control Protocol — has long been the communications standard for data transfer between devices and applications on a network. Used in billions of devices, it’s become the de facto network transport protocol, ensuring data reaches its destination as quickly as possible.
That was until Google stepped into the arena.
QUIC — Quick UDP Internet Connections — is a relatively new transport layer network protocol designed and implemented by Google. Despite being around since 2012, it’s only recently become ubiquitous and is now used in most connections between Google Chrome to Google’s servers. Since Chrome remains the world’s most-used internet browser, QUIC — pronounced quick — has become a pretty big deal.
Due to its rapid uptake and increased level of encryption, Google QUIC has created a hole in existing network security appliances, such as threat intelligence tools and firewalls. Unfortunately, hackers can exploit QUIC’s additional layer of encryption, which raises all kinds of network security concerns. In this guide, you can learn more about QUIC and its affect on network security.
What is Google QUIC?
Google developed QUIC with good intentions. It started as an alternative to TCP+TLS+HTTP/2 to improve user performance and web page loading times on the Chrome browser. Google claimed QUIC offered advantages over TCP because it’s built on top of UDP (User Datagram Protocol). QUIC performs better than TCP when it comes to multiplexing and connection handshakes.
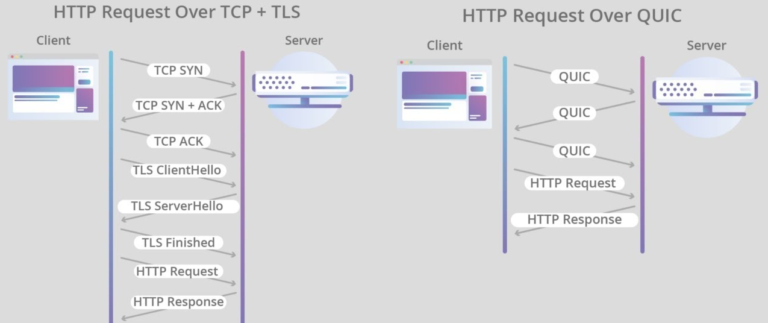
Moreover, QUIC is quicker to establish a secure connection than TCP and reduces the overhead when setting up connections. When additional sessions are needed, QUIC uses the same encryption setup as previous sessions so only 2 packets are needed for session initiation, rather than the standard 6 or 7 used for TCP. This drastically reduces overall latency and enhances the user’s internet browsing experience (all good things for Google!).
Why do Network Security Teams Not Like Google QUIC?
Despite its perceived positives, QUIC could inadvertently have a negative impact on network security. That’s because security appliances like firewalls and network sensors typically are not able to access information they had previously relied on with legacy TCP sessions. This creates a ‘black hole’ that hackers can exploit.
Here’s the main problem: Standard network security devices can’t determine the QUIC application protocol, viewing it like layer 4 UDP traffic. While browsers and supported web servers can differentiate between QUIC traffic and other traffic, standard network security like firewalls can’t.
This means firewalls are less effective at detecting incoming threats, putting network security at risk. To complicate the challenge for cyber threat hunters, Google revises its protocol frequently, and threat detection tools must catch up with these ever-changing standards. There are other issues.
QUIC, similar to TLS 1.3, applies its encryption at the transport layer and not in the higher layers. Hence, it encrypts all transport information, which can virtually eliminate the attack surface that TCP offers. Plus, it’s increasingly difficult to measure and analyze QUIC traffic using reporting tools because, again, firewalls and standard network sensors don’t recognize it. This is a plus for consumer privacy but causes significant challenges for those responsible for protecting our communications networks.

Interested in how QUIC-based metadata can be used to detect IoCs?
It’s no wonder, then, that some network security teams have advised administrators to disable or block QUIC and return to HTTPS over TCP.
Final Word
While touted as an alternative to TCP, QUIC poses several security concerns for network operators. Standard network security appliances cannot easily identify QUIC traffic, which makes this network protocol vulnerable to cyber criminal activity.
Want to upgrade your threat intelligence? Get greater visibility into your networks with NetQuest’s Streaming Network Sensors. Learn more.
