Since late 2024, the cybersecurity community is paying increasing attention to two prominent threat actor groups: Volt Typhoon and Salt Typhoon. Both are widely attributed to Chinese state-sponsored efforts and represent a growing trend in nation-state cyber operations focused on persistence, stealth, and pre-positioning. Understanding these threats—and how to counter them—has become essential for anyone tasked with defending critical infrastructure and telecommunications networks.
What is Volt Typhoon?
Volt Typhoon came to global prominence in mid-2023 when Microsoft and other industry leaders disclosed a long-term, covert cyber espionage campaign targeting U.S. critical infrastructure sectors. This group, assessed to be affiliated with China, has demonstrated a high degree of operational maturity and restraint.
Volt Typhoon primarily focuses on targeting critical infrastructure in the following areas:
- Energy
- Water
- Transportation
- Communications
- Government & Military Installations
Its activity spans both the continental United States and allied nations in the Indo-Pacific region. The overarching objective appears to be pre-positioning—gaining persistent access to vital systems to enable potential future disruption in the event of geopolitical escalation.
Tactics, Techniques, and Procedures (TTPs):
Volt Typhoon is notable for using “living off the land” (LOTL) techniques. Instead of relying on malware that can be detected and quarantined, it leverages legitimate tools built into the operating system—such as:
- PowerShell
- Windows Management Instrumentation (WMI)
- Scheduled Tasks
- Command-line utilities
By avoiding traditional malware, Volt Typhoon evades many commercial detection mechanisms, making it particularly dangerous in environments where deep packet inspection and east-west traffic monitoring are lacking.
In one notable campaign, Volt Typhoon maintained undetected access in the U.S. electric grid for nearly 300 days, highlighting the challenge of identifying these types of stealthy intrusions.
What is Salt Typhoon?
While Volt Typhoon targets critical infrastructure, Salt Typhoon has been identified as a telecom-specific espionage operation. We have talked about Salt Typhoon before, which is also attributed to Chinese state-sponsored actors. Salt Typhoon focuses on accessing information from the following network segments:
- Major U.S. telecommunications providers
- Fiber backbone infrastructure
- Data routing and switching systems
First exposed in a 2024 investigation by UMBC cybersecurity experts, Salt Typhoon reportedly gained unauthorized access to network devices, including routers and switches, at several tier-one telecom providers such as AT&T, Verizon, and Lumen Technologies.
Tactics and Impact:
Salt Typhoon’s operations exploit:
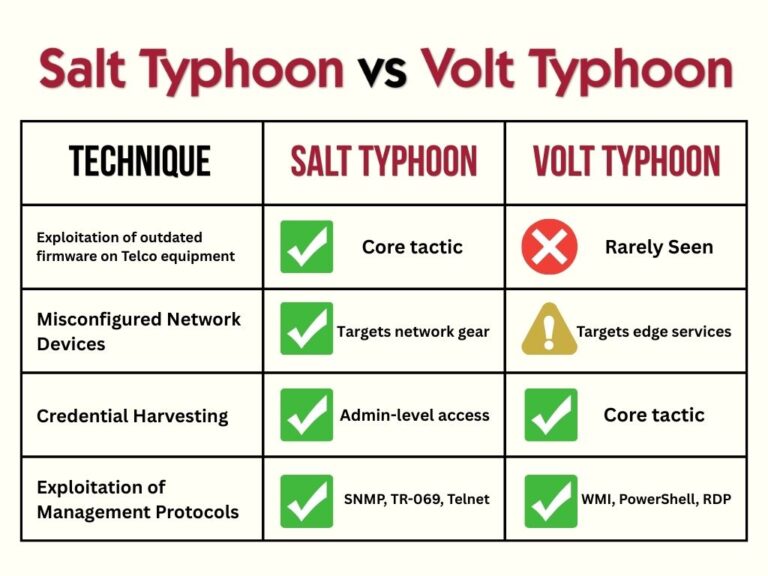
- Outdated firmware on telecom equipment
- Misconfigured network devices
- NetOps user credential harvesting
- Exploitation of remote management protocols
Once inside the infrastructure, bad actors extract metadata, call detail records (CDRs), and potentially real-time communication traffic.
This kind of access has two-fold consequences:
- Intelligence Gathering – Surveillance of conversations, metadata, and infrastructure planning.
- Disruption Potential – Pre-positioning within telecom systems could allow future degradation of voice, data, or emergency services during a conflict.
Both groups appear to be part of a larger strategic initiative to prepare for cyber conflict scenarios by gaining silent access across sectors vital to U.S. national security and communications.
How Cybersecurity Professionals Can Defend Against These Threats
Mitigating these kinds of persistent and stealthy adversaries requires a shift in mindset. Traditional perimeter-based defenses and antivirus software are no longer sufficient. Here are best practices that security professionals responsible for defending critical infrastructure can implement:
- Zero Trust Architecture: Move away from implicit trust models. Assume breach and segment internal networks so that compromise in one zone does not give access to all.
- Network Visibility and East-West Monitoring: Threat actors like Volt and Salt Typhoon thrive in environments without internal monitoring. Organizations must deploy tools that can:
- Capture metadata from internal network traffic
- Minimize traffic sampling that enable blind spots
- Identify anomalous lateral movement
- Monitor device-to-device communication
- Threat Hunting & Behavior Analysis: Active threat hunting using encrypted traffic analysis , TLS fingerprinting and behavior-based detection models can uncover subtle signs of persistence or lateral movement not flagged by signature-based tools.
- Firmware and Configuration Auditing: Regular auditing of network devices—routers, firewalls, and switches—can help identify unauthorized changes, outdated firmware, and suspicious configurations.
Where NetQuest Fits In
To confront adversaries like Volt Typhoon and Salt Typhoon, organizations need tools that go deeper into network infrastructure—beyond simple log analysis or endpoint detection.
NetQuest’s Streaming Network Sensors provides advanced network visibility solutions that enable cyber threat hunting tactics that observe traffic at the optical and packet level, even in high-throughput environments like telecom backbones and critical infrastructure facilities, with capabilities like passive optical tapping, JA4+ fingerprinting, real-time DPI-enriched metadata extraction and seamless integration with analytics tools like Suricata or 3rd party data warehouses.
NetQuest’s solutions allow defenders to analyze the internal communications Volt Typhoon relies on and detect lateral movement typical of Salt Typhoon operations. Maintain full visibility without introducing prohibitive costs or detection gaps.
By feeding enriched metadata into SIEM, SOAR, and behavioral analytics platforms, NetQuest’s DPI-based probes help cyber threat hunting teams gain the context and telemetry necessary to detect advanced threats early—before data is exfiltrated or systems are disrupted.
