NetQuest Streaming Network Sensor
Security-Optimized Flow Data for Cyber Security and Threat Intelligence
Unlock the Power of Network Intelligence With the Best Network Flow Sensor
The NetQuest Streaming Network Sensor delivers breakthrough performance for high-scale, complex networking visibility requirements and is the best network data source for security tools that rely on accurate and reliable network intelligence.
The Streaming Network Sensor monitors all traffic across the physical network to translate petabytes of network traffic into compact and highly efficient metadata. As an abstraction of network traffic, the Metadata contains detailed information about network activity for both clear and encrypted traffic for powerful always-on visibility.
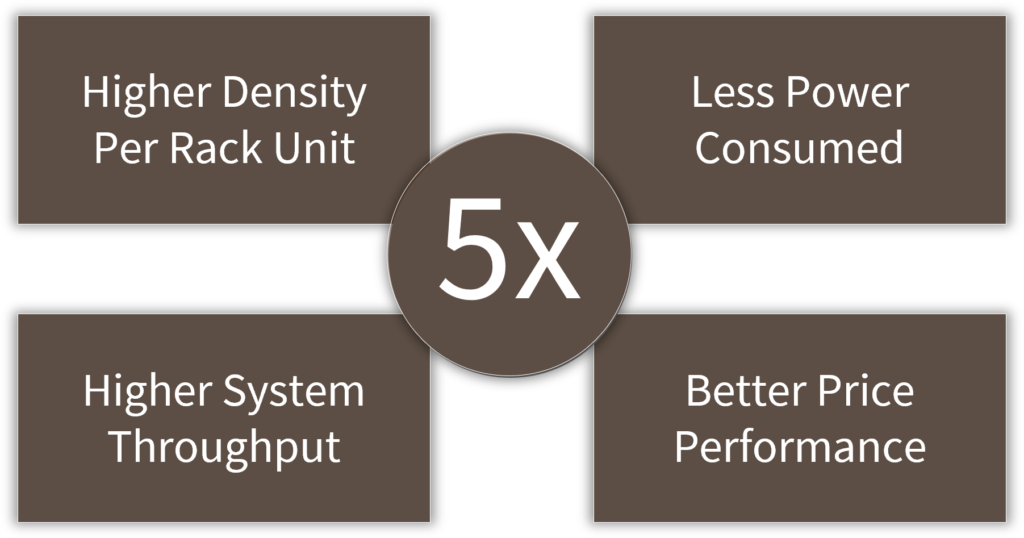
The Streaming Network Sensor sets the standard for IPFIX network flow sensors with 5x higher network metadata creation
capacity and 5x better price performance
over alternative network flow sensors.
Unmatched Scale & Performance

The Streaming Network Sensor is purpose-built for ultra-scale deep network traffic analysis for 10G, 25G, 40G, 100G and 400G network monitoring environments. Leveraging the NetQuest OMX platform’s powerful FPGA-based distributed pipeline processing architecture, the Streaming Network Sensor analyzes network traffic in a single pass without consuming multiple analysis ports for different services. Deep Packet Inspection services and metadata creation are performed simultaneously at wire-speed delivering unmatched sustained performance at scale.
The Streaming Network Sensor delivers more than 5x higher density, throughput, and packet processing power per rack unit enabling 1.6 Tbps of sustained network traffic processing analyzing up to 17 petabytes of network traffic per day.
Flow Metadata Generation Pipeline Process

16x
100G
Highest Density
100G and 10G Per RU
1.6
Tbps
Delivers the highest scale IPFIX traffic processing
800
Million
Active Flows delivers the highest throughput
Scale-Out Performance
Modular architecture enables linear expansion and scale
Optimized for Security Monitoring
The Streaming Network Sensor is purpose-built to support intensive security monitoring requirements. The sensor enables cost-effective and ultra-scale visibility to see all traffic in motion and extract the metrics that matter most with packet-like accuracy.
The context-rich metadata provides the richest possible data set to power your security tools with the high-fidelity traffic intelligence needed to speed the detection of emerging threats, identify high-risk behavior, uncover ‘low and slow’ attack vectors, identify indicators of compromise, and support investigative activities.

Example Use Cases
Threat Hunting
and Detection
Threat Hunting
and Detection
Continuous Monitoring
Continuous Monitoring
Incident Response and Remediation
Incident Response and Remediation
Encrypted
Traffic Analysis
Encrypted
Traffic Analysis
Historical Forensic Analysis
Historical
Forensic Analysis
Regulatory and Compliance
Regulatory and Compliance
IP
Data Records
IP
Data Records
Lawful Intelligence
Lawful
Intelligence
Fraud Detection and Investigation
Fraud Detection and Investigation
Unsampled Flow for Deep Network Intelligence and Visibility

The Streaming Network Sensor observes all traffic and processes EVERY packet and flow in real-time as it crosses the wire. Analyzed traffic is converted to 1:1 unsampled Flow metadata for 100% of the packets observed at line rate with no dropped packets or data loss.
Users can choose from thousands of traffic data attributes to extract relevant metrics from network traffic to reveal contextual connection and user activity intelligence for every network flow and transaction with packet-level accuracy.
Analysts can define the output metadata fields to be delivered to tools based upon flexible criteria allowing different data sets to be sent to different tools to meet operational requirements.
Expand Your Network Intelligence and Threat Detection Capabilities
- Network statistics
- Specific protocols and services
- Application-level metadata
- Encrypted traffic handshakes and headers
- Subscriber information for fixed and mobile traffic

Real-Time Deep
Packet Inspection
Hardware-based wire-speed Deep Packet Inspection enables IPv4 and IPv6 traffic analysis inside tunnels and beyond packet headers to reveal the inner IP payload and headers
exposing unobstructed Layer 2-7 network traffic insights.

Packet-Like
Fidelity
1:1 unsampled Flow data is an abstraction of network traffic based upon full packet analysis of wire data and identifies users, protocols, services, and provides application context providing a complete and accurate summary of all
network activity.

The Power of the Packet
Without the Storage Burden
Flow metadata is compact and highly efficient and represents less than 1% of monitored network traffic volumes. The context-rich metadata retains up to
95% fidelity compared to captured packets but with dramatically less physical storage.
Powerful Metadata Works With
Existing Security Tools
The Streaming Network Sensor is a universal network data source that delivers standards-based IPFIX Flow metadata. The exported Flow datasets provide rich and accurate metrics that are easily consumed by a wide range of Flow collectors and tools such as XDR, NDR, SIEM, SOAR, Threat Detection and security monitoring & analysis platforms. Flow metadata can also be sent to common database environments, such as centralized or distributed data lakes and data warehouses that collect intelligence datasets for multiple upstream applications.

Customizable
Data Sets
Customizable data templates
allow users to choose from 100s
of metrics and elements to
support each platform’s network intelligence requirements.
Intelligent Metadata Optimization
Metadata output can be customized and filtered to report only the specific metadata fields of interest, or load balanced across up to 16 collectors to streamline collection and
optimize storage.

One Sensor Supports
Multiple Platforms
Different customized metadata sets
can be sent to different flow collectors to support diverse security tool platform data requirements
or redundant high availability requirements.
Put the Power of Enriched Flow Intelligence
in your Analysts' Tool Kit
Application-level and encrypted traffic visibility accelerates and automates the detection of threats, anomalous activity, and evasive traffic powering deep network and user traffic intelligence use cases.
Combining Deep Packet Inspection with advanced analytical techniques and machine learning, Enriched Flow Intelligence can be added to any Streaming Network Sensor. Enriched Flow Intelligence automatically discovers and reveals application classifications, protocol-specific attributes, and encrypted traffic metrics for clear and encrypted traffic. Real-time layer 4-7 analysis is performed in hardware at ultra-scale speeds with no performance impacts or reduction in sensor capacity.

Application Layer and Encrypted Traffic Enrichment
Application Layer Enrichment
Layer 4-7 enrichment provides
contextual metadata that powers
deep security intelligence with protocol
and application-specific attributes for
thousands of applications and
services crossing the network.

Encrypted Traffic Analysis
Encrypted Traffic Analysis (ETA) automatically
identifies encrypted flows and extracts fingerprints
signatures, and heuristics to accelerate threat detection
and identify potential indicators of compromise without
the need for slow and expensive decryption. This enables
identifying threats hiding in encrypted traffic such as
command and control attacks, malware, and
data exfiltration.
Simultaneous Real-Time Packet-Flow Delivery
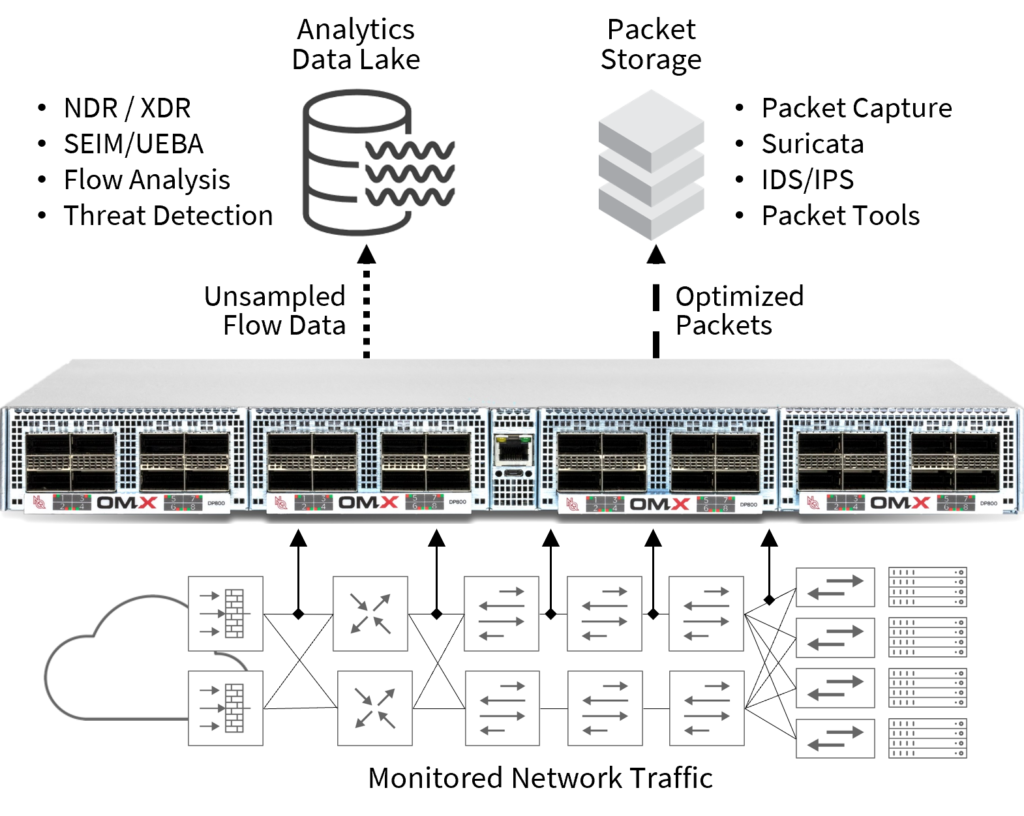
Leveraging the software-defined flexibility of the NetQuest OMX Platform, the Streaming Network Sensor can simultaneously deliver optimized packet-flow traffic to packet capture probes and packet-based analysis tools from the same network traffic processed for Flow metadata creation with no performance trade-offs.
Metadata creation and packet optimization services are applied to network traffic in one pass, without impacting metadata creation performance. Packet-flow traffic can be filtered, sliced and optimized to deliver only the targeted and relevant packet-flows as required by upstream tools to reduce the burden of collecting unwanted packets. Packet traffic can be cross-tagged with metadata to enable the correlation of metadata to packets in upstream tools for rapid forensics.
Extensibility to Support Network Packet Collection
Supports multiple monitoring
and analytics requirements from
a single point of instrumentation
using the same network traffic.

No Extra
Ports Needed
Packet-flow traffic is delivered from
the same input port, so packet
delivery does not reduce system
port capacity.

Simplify Operations
and Accelerate ROI
Reduce complexities and lower
TCO associated with managing multiple sensors, probes, and
Network Packet Brokers.
The NetQuest Advantage
While Others Claim Highest Performance and Capacity, NetQuest Actually Delivers It!