As Internet usage continues to expand exponentially at breakneck speed — particularly in the business sector — companies should be prepared not only for new revenue generation and growth opportunities, but also for facing challenges with network security and reliability. Just as applications, compute infrastructure, and the number of connected devices increase, the network scales as well, typically exponentially. Maintaining cyber security threat identification at scale is important to track as your network infrastructure evolves via on-premises expansion or cloud migration. It is imperative to ensure the protection of critical data and to minimize the risk of a security breach as your network complexity increases.
Here is what you need to know about network monitoring and cybersecurity threat identification as your network evolves.
Using Flow-Based Analysis vs. Packet-Based Analysis to Detect Cyber Security Threats
Monitoring your network for potential threats is critical to your corporate health as the network is literally the corporation’s lifeblood. Older security guidance recommended viewing every packet to detect all network anomalies and expose potential security threats. Newer methodologies have emerged favoring inspection of flow-based data (information summarizing each network conversation) over packet-based data. Monitoring network flows can be equated to measuring your temperature and blood pressure to quickly detect health, rather than using detailed lab tests and x-rays for every doctor visit. Both packet-based and flow-based tactics have advantages and drawbacks for network security analytics; here is a quick look at each and how to combine them for maximum efficacy and scalability.
Packet-Based Analysis
Pros
- Packet-based analysis has been preferred by many IT professionals for years simply because it is so thorough; this type of analysis does not miss any important details.
- Firewalls and Intrusion Detection systems are at their core – packet analyzers.
- The packets contain all the information for every transaction in your business.
Cons
- Processing packets for securing high-speed networks or carrier backbones requires stacks of costly servers for storage and analysis.
- Processing packets within standard cloud infrastructure is expensive due to the cost of bandwidth – you are paying for traffic twice.
- Packet-based visibility systems cannot view encrypted traffic which can consist of over 50% of all traffic on typical network links.
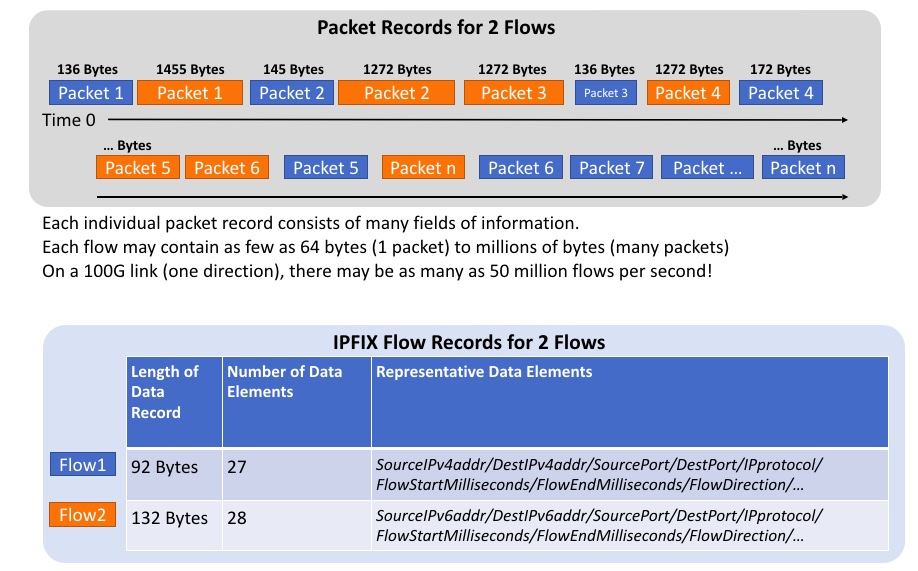
Flow-Based Analysis
Pros
- Flow-based analysis provides a summary of packets within a flow and can reduce network traffic to your security tools by nearly 98% while still providing 100% visibility to subtle threats.
- Modern flow-based analysis can identify applications and other useful application-layer information even if the traffic is encrypted.
- Flow-based data can be created, collected, stored, and analyzed at a significantly lower cost than packets.
Cons
- For fine-grain detail that is required to detect a particular malware variant or other data located deep within a packet, a packet-based system is required.
- Some network flow deployments rely on sampled collection, only viewing 1 out of every 1k or 1 out of every 10k packets. Unfortunately, this is not useful in standard security applications.
Using Flow-Based Analysis to Complement Packet-Based Analysis: The Best of Both Worlds
Fortunately, your organization does not have to choose between flow-based or packet-based analysis. You can have the best of both worlds by using a network service node (a probe with more capability) — a network device that reconfigures raw packets into unsampled flow data, while at the same time steering targeted packets for deeper level forensics. A network service node can also “clean” packet data by stripping headers and tunnels to access innermost IP packets for delivery to downstream analytics tools. Complementing packet-based analysis with flow metadata is an excellent strategy for comprehensive network monitoring that can be scaled as needed.
What Is IPFIX?
Internet Protocol Flow Information Export (IPFIX) is an IETF standard defining a mechanism for extracting detailed flow information from network routers, switches, and probes. IPFIX is based on NetFlow, a Cisco-created network protocol designed to network performance by monitor incoming and outgoing IP network traffic.
Understand the difference between NetFlow and IPFIX
How IPFIX Is Used
Managed IT security providers and other IT professionals use unsampled IPFIX flow data to:
- Observe network traffic 24/7/365 in real-time
- Preserve a picture of the network at any given time
- Detect low-and-slow security attacks against the network, web servers, or Enterprise IT system.
- Provide multiple layers of defense against internal and external cyber security threats
- Collect data about network flows to allow for adequate traffic engineering and capacity planning
Sampled or Unsampled Flows?
Sampled flow data is a technique used by switches and routers to provide general information about a network’s behavior by inspecting a small representative percentage of the traffic – usually 1 of every 1k or 1 out of 10k packets. This enables traffic engineers to gain visibility into how the network is being used. The drawback in using sampled flow data is that this technique is not useful for fine-grain security threat analysis.
Unsampled flow data is a technique typically supported by more advanced network probes, sensors or service nodes. These appliances provide information detailing every flow traversing the network link. SecOps teams are increasingly using unsampled flow data to maintain cyber security threat identification at scale.
Get Help with Your Network Monitoring Today
NetQuest has over 30 years of providing high-speed WAN monitoring and service provider backbone packet processing for scalable network visibility. NetQuest’s OMX3200 IPFIX sensor generates unsampled flow data to security analytics tools helping SecOps teams avoid network blind spots. Learn more about intelligently scaling your network visibility fabric and safeguarding your company from malicious cyber threats by contacting NetQuest today.
Chip Mesec, Senior Product Manager, NetQuest Corporation
