As cybercriminals become increasingly skilled at exploiting encrypted data, fingerprinting techniques play a crucial role in detecting and preventing such attacks. As technology continues to evolve at a rapid pace, so does fingerprinting technology.
In September 2023, John Althouse with FoxIO announced a new suite of threat hunting fingerprints called JA4+. Here’s what you need to know about the update to the groundbreaking fingerprinting technology.
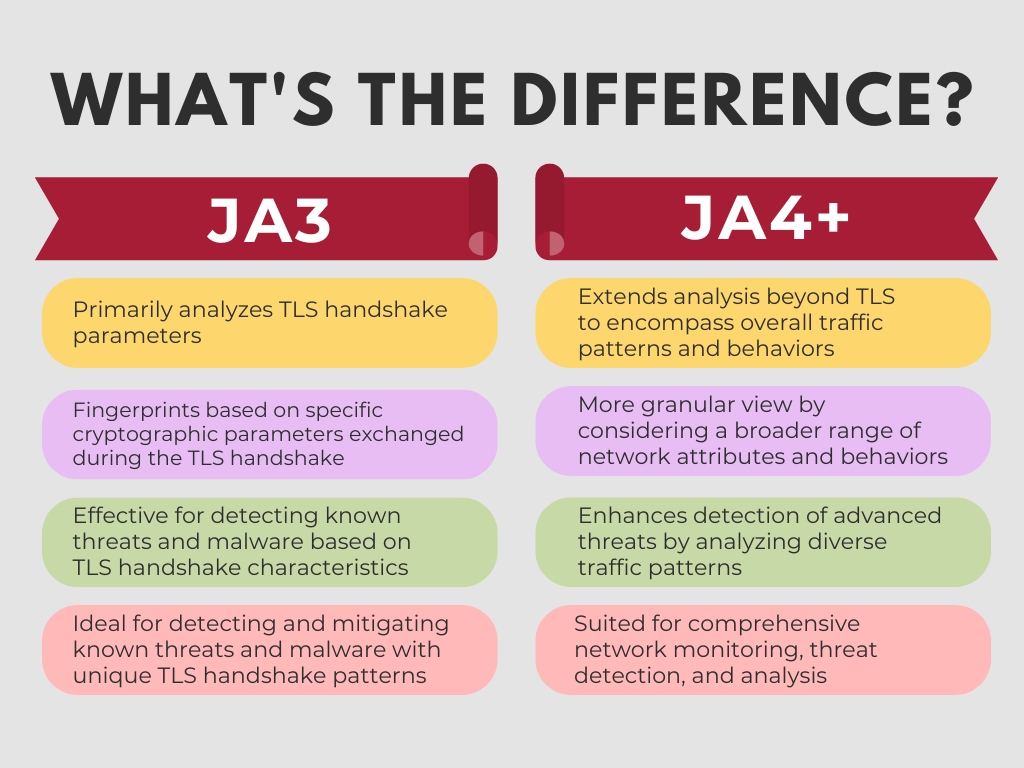
Brief Overview of JA3
We have discussed the impact JA3 fingerprinting brought to the cybersecurity space in the past and much of what was said regarding JA3’s ability to help threat hunters deal with TLS encrypted traffic still rings true today. JA3 made waves in the cybersecurity community as a robust method for fingerprinting TLS clients based on their behavior during the initial handshake process. By analyzing cryptographic parameters such as the client’s supported ciphers and extensions, JA3 could generate a unique fingerprint for each TLS client application.
The solution leverages the handshake process between a client and a server. During these handshakes, various parameters must be negotiated, such as the TLS version, TLS extension lengths, cipher suites, elliptic curve groups, and elliptic curve point formats. These handshake details are then transformed into 32-character MD5 hashes, creating JA3 fingerprints for both the client and server sides. Equipped with these JA3 fingerprints, this technique proved invaluable for detecting and abating threats like malware and botnets.
Introducing JA4+
Building upon the success of JA3, JA4+ emerges as the next evolutionary step in network traffic fingerprinting for threat hunting. While JA3 focused primarily on the TLS handshake, JA4+ extends its scope to encompass broader network traffic analysis. This evolution enables JA4+ to provide a more comprehensive view of network activity, making it adept at identifying advanced threats and sophisticated adversaries.
In a quote from one of the creators, John Althouse, in an interview with Hunt.io, said “There will finally be a fingerprint database with curated data and API access. JA4+ allows for passive network detection of a wide range of threats, not just malware.”
Leveraging Both Fingerprints for Network Security Threat Hunting
Unlike the case with most technological innovations and advancements, JA4+ is not here to immediately replace JA3, but to piggy-back off its features, provide additional analysis depth and provide a migration path to a more comprehensive network security plan. Here’s three key areas security teams can utilize both for:
- Threat Detection: Organizations can utilize both JA3 and JA4+ to bolster their threat detection capabilities. While JA3 excels at identifying known threats based on TLS handshake patterns, JA4+ provides a broader context for analyzing network action, enabling detection of more sophisticated threats.
- Incident Response: Incorporating JA3 and JA4+ into incident response procedures enhances the ability to quickly identify and respond to security incidents. The combination of these techniques offers a multi-faceted approach to understanding network behavior and potential threats.
- Threat Intelligence: By leveraging JA3 and JA4+ signatures, cybersecurity teams can contribute valuable threat intelligence to enhance the security posture of not only their organization, but also the broader community. Sharing insights derived from network fingerprinting helps in collectively combating emerging threats and theoretically predicting and mitigating future threats.
Optimize Network Visibility with JA4+ Fingerprinting!
As growing volumes of data continue to become more encrypted, security teams of large government and telecommunications tasked with “finding the needle in the haystack” are challenged by searching for smaller “needles” in massive “haystacks.” Expanding attack surfaces have forced teams’ hands to create a proactive approach to network security.
NetQuest’s Streaming Network Sensors can identify encrypted traffic and extracts both JA3 and JA4+ fingerprints, signatures, and heuristics to accelerate threat detection. The sensors allow the identification of indicators of compromise and expose threats hiding in encrypted traffic through context-rich metadata without the need for slow and expensive decryption.
The context-rich metadata delivers a comprehensive data set, enhancing your security tools with high-fidelity traffic intelligence. This accelerates the detection of emerging threats, identifies high-risk behaviors, uncovers ‘low and slow’ attack vectors, pinpoints indicators of compromise, and supports investigative activities.
