The term Dark Web often conjures up an image of illicit activities or malicious actions carried out online by cybercriminals. Negative publicity surrounding it – largely in the news for instances of financial data leakage, drug peddling, organ selling, hiring criminals, buying & selling illegal weapons, etc. – has rightfully created this perception. But the reality is that network security teams can use the Dark Web, and its unique set of intelligence, to strengthen its defense against cyber threats.
What is the Dark Web?
The Dark Web is a distinct form of the web, where no search engine indexes the content on this portion of the network. Dark Web browsing requires special software, authorization, and specific network configurations to access – primarily The Onion Router (Tor). In other words, it is a unique collection of onion-routed websites that require a Tor browser to access. Cybercriminals prefer such a web network as it evades all government and private censorship, tracking, and preserves anonymity.
Understanding the Dark Web gives you insight into the unlawful purposes it serves for cybercriminals as well as its legitimate influence on cybersecurity. In fact, since it is almost impossible to track activity on the Dark Web, it has become an ideal arena for the cyber underworld.
Difference Between Surface and Dark
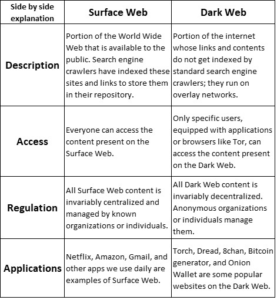
Access to the Dark Web can provide invaluable insights for network security and cyber threat hunting teams.
Here are some ways a cyber security team can leverage the Dark Web to increase threat intelligence:
- Prepare a checklist of all the different websites or forums where attackers publish zero-day vulnerabilities of various products and apps. Can enable setup of precautionary safeguards.
- It can assist security experts in analyzing and exploring the latest tools and methods cybercriminals use to attack a system. Miscellaneous services and tools like Ransomware-as-a-Service, DDoS-as-a-Service, Malware-as-a-Service, etc., are available on the Dark Web for hackers. Analyzing these types of tools and services will help security teams build a strong security foundation for their organization.
- Using it for cyber threat intelligence mining. This is a process through which security professionals harvest data for insight on even the most inaccessible corners of the internet. The process will provide them with actionable intelligence to strengthen their cyber security position.
- Search for activity relating to a particular company or its customers that may be targeted by special tools and datasets created by hackers for sale. Also, finding vulnerabilities or tools directed toward exploiting specific corporate IT assets also provides a “look forward” at what type of attacks may be used against a specific network.
Key Historical Developments
- Silk Road
Started in 2011, Silk Road was the first online underground marketplace from where users could buy anything they wanted. It was emblematic of the power of anonymity and how the Dark Web helped criminals achieve that. Silk Road was doing $1.3 billion annual revenue before being shut down in 2013.
- Bitcoin
Buying something from a black market like Silk Road using a regular wallet or credit card is traceable. So, in 2011, Silk Road became the first marketplace to allow transactions using Bitcoin. This contributed to the popularity of cryptocurrencies.
The Future of The Dark Web
The Dark Web’s aim was to provide anonymity and preserve privacy in cyberspace, where every organization leverages data to track user actions and online behavior. As users become more aware and understand the importance of digital privacy, more people may transition to there to evade prying eyes, all-pervasive surveillance, and gain more control over their identity data.
Cyber security teams want to keep an eye on what is going on in the cyber underworld and have insight into what hackers are targeting. Unfortunately, this contradicts consumers rights to online privacy. In the meantime, it is imperative that network security teams leverage the Dark Web as a vehicle for knowledge and threat intelligence.
